Device Protect
Table of contents
Introduction
With most of the business PCs now mobile, portable devices present distinct challenges to network security, which must account for all the locations and uses that employee require of the company network. Potential threats to devices include malicious mobile apps, phishing scams, data leakage, spyware, and unsecured Wi-Fi networks. On top of that, Enterprises must account for the possibility of an employee losing a device or if a device is stolen. To avoid a security breach, companies should take clear, preventative steps to reduce the risk.
SKU’s
The following SKUs for Identity Protect has been defined:
| Feature | Device Protect (Standard) |
|---|---|
| Protection against malware | + |
| Protection against ransomware | + |
| Always secure settings | + |
| Proactive vulnerability management | + |
| Mobile device support | + |
| Monitoring VIP devices | - |
| Extended Coverage (with usecases) | + |
| Compliant with NEN & ISO | + |
| 24/7 incident follow-up | + |
Features
Protection against malware
Malware (a portmanteau for malicious software) is any software intentionally designed to cause damage to a computer, server, client, or computer network (by contrast, software that causes unintentional harm due to some deficiency is typically described as a software bug). Devices infected with malware can potentially install ransomware or let attackers have access to business-critical information.
Wortell uses Defender for Endpoint as their primary endpoint detection and response solution (EDR). As part of Device Protect, Wortell will investigate and respond (mitigate) all malware that is detected by the EDR solution that is in place. Wortell has trained security engineers who know how to respond to advanced malware. Responding quickly and with a decent (proven) response plan will reduce the risk and impact that malware can have.
Protection against ransomware
Ransomware affects an infected computer system in some way and demands payment to bring it back to its normal state. There are two variations of ransomware, being crypto-ransomware and locker ransomware. With the locker ransomware just locking down a computer system without encrypting its contents. Whereas traditional ransomware locks down a system and encrypts its contents. For example, programs such as CryptoLocker encrypt files securely and only decrypt them on payment of a substantial sum of money.
Wortell uses Defender for Endpoint to protect your valuable data from malicious apps and threats, such as ransomware. Controlled folder access protects your data by checking apps against a list of known, trusted apps. Controlled folder access works by only allowing trusted apps to access protected folders. Protected folders are specified when controlled folder access is configured. Typically, commonly used folders, such as those used for documents, pictures, downloads, and so on, are included in the list of controlled folders.
Controlled folder access is especially useful in helping to protect your documents and information from ransomware. In a ransomware attack, your files can get encrypted and held hostage. With controlled folder access in place, a notification appears on the computer where an app attempted to make changes to a file in a protected folder.
Wortell has trained security engineers who know how to respond to advanced ransomware attacks. Even though a lot of protection is in place to prevent ransomware from running, cybersecurity is still a cat and mouse game. Especially in case of a ransomware incident, it is important to act quickly and correctly.
Monitoring for data leakage
Business-critical data is important. The impact of a data leakage where business-critical data is leaked can be enormous. Wortell can detect data leakage of business-critical data when Azure Information Protection is used in your organization.
As data is classified earlier, it is known what files are business-critical, confidential, etc. Wortell makes sure that Microsoft Defender for Endpoint is connected to Azure Information Protection. Each incident or alert raised by Microsoft Defender Security Center includes a ‘data sensitivity’ attribute that is generated by aggregating the sensitivity of all the labeled files discovered on devices that are affected by the incident. This allows security analysts to increase the severity of an incident based on data sensitivity.
ncreasing the severity might result in escalating the incident from “tier 1” to “tier 2”. A consequence of this might be that the incident no longer meets the criteria of an incident that gets resolved for free as part of the subscription.
The data leakage monitoring feature is only available when Azure Information protection is configured and used by the customer.
Always secure settings
As part of the onboarding, Wortell will make sure the security-related settings are configured conform the Microsoft baseline and Wortell best practices. This configuration consists of settings that will make sure all devices are protected well and Wortell can respond to incidents occurring on these devices.
As your IT department builds on the IT infrastructure of your company, it might be that some settings are changed. Another reason why settings can be changed is that an attacker was able to change settings and increase the risk to cyber attacks in your organization. Therefore, Wortell will periodically check all settings of the solutions that are being used to provide device protection.
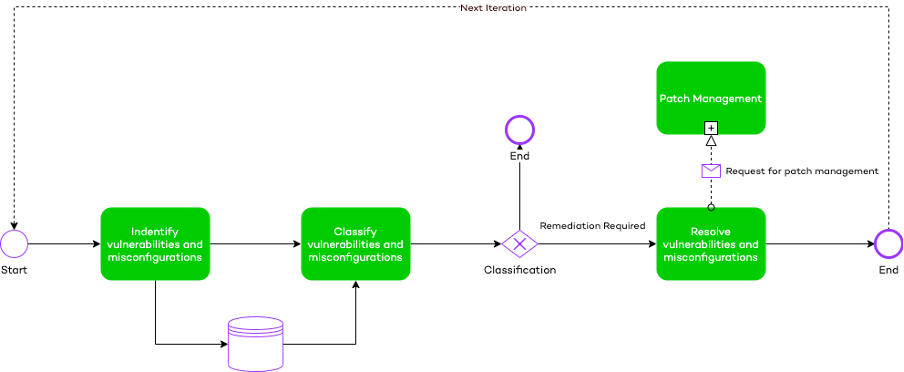
Proactive Vulnerability Management
Threat and vulnerability management is the process of identifying, classifying, and resolving misconfigurations and vulnerabilities. In cybersecurity, a vulnerability is a weakness that can be exploited by a malicious actor to gain unauthorized access to or perform unauthorized actions on a computer system. Vulnerabilities can allow attackers to run code, access a system’s memory, install malware, and steal, destroy or modify sensitive data.
To exploit a vulnerability an attacker must be able to connect to the computer system. Vulnerabilities can be exploited by a variety of methods including SQL injection, buffer overflows, cross-site scripting (XSS) and open-source exploit kits that look for known vulnerabilities and security weaknesses in web applications.
A misconfiguration is a setting that is set and will make the IT environment vulnerable. An example of a misconfiguration can be: “a firewall rule that opens port 3389 on a public IP address”. Open misconfigurations become dangerous when legitimate services are exploited through security vulnerabilities or malicious services are introduced to a system via malware or social engineering, attackers can use these services in conjunction with misconfigurations to gain unauthorized access to sensitive data.
Threat and Vulnerability management is proactive, seeking to close the security gaps that exist before they are taken advantage of. If not remediated well, misconfigurations and vulnerabilities will increase the risk and chance of getting attacked.
Wortell provides a process that will reduce the number of vulnerabilities and misconfigurations on your devices. This process will help:
- Reduce the chance of getting attacked successfully by resolving misconfigurations. This will make it harder or even impossible to exploit vulnerabilities.
- Reduce the risk of getting attacked by resolving known vulnerabilities.
- Reduce the impact of an attack by resolving misconfigurations and vulnerabilities. This will make it harder or even impossible to traverse through the IT network.
- Reduce the number of alerts generated by various security products. By resolving vulnerabilities and misconfigurations, sensors are less likely to trigger, because actors are not able to execute actions that will trigger them.
- Report on the risks found in an IT environment.
Mobile device support
Users of your company are most likely to use other devices aside from their regular workstation/laptop computer. Just like regular devices, mobile devices can also access business-critical data. It is therefore important to respond quickly and correct when potential malicious behavior is seen on mobile devices.
Wortell will configure Microsoft Defender for Endpoint for iOS and Android will with protection against phishing and unsafe network connections from websites, emails, and apps on Android/IOS devices.
Trained Wortell security engineers will respond to alerts and incidents generated by mobile devices.
Monitoring VIP user devices
Each organization has employees/accounts that have more than the normal set of privileges or have access to important data (crown jewels). As an attack on devices of these users can have a high impact on the business due to their access to critical information, they require more attention during incident response.
When an incident occurs for a VIP user device, the severity will get increased by one level. For example: when an incident happens with a medium severity, the severity will get increased to high when a VIP account is involved.
Increasing the severity might result in escalating the incident from “tier 1” to “tier 2”. A consequence of this might be that the incident no longer meets the criteria of an incident that gets resolved for free as part of the subscription. It is therefore important to have a decent balance between VIP accounts and regular accounts.
Extended Coverage (with usecases)
Wortell conducts it’s own security research. The goal of this ongoing security research is to understand the way how attackers operate and use that knowledge to build usecases for these attacks. A usecase, in the security world, covers an attack method or analysis. The usecase contains all the logic (instructions) to detect the attack and tasks te respond on this attack. Security products that are being used by Wortell Managed Detection and Response cover a wide range of attacks. By conducting our own security research and usecase development Wortell is able to add value on top of these security products.
Security research and usecase development is an ongoing process; new usecases will be added periodically.
24/7 incident follow-up
Identities are important, and attacks are happening during the day and nighttime. Therefore, Wortell has a team of cybersecurity engineers available 24/7.
Wortell has organized the availability of the experts as follows:
- Tier 1: Eyes on-screen during business hours and outside of business hours
- Tier 2: Eyes on-screen during business hours, stand-by outside of business hours
- Tier 3: Eyes on-screen during business hours, stand-by outside of business hours
ISO and NEN compliant
ISO/IEC 27001 is widely known, providing requirements for an information security management system (ISMS). Using it enables organizations of any kind to manage the security of assets such as financial information, intellectual property, employee details, or information entrusted by third parties.
All processes and actions that are in place for Device Protect are NEN and ISO compliant.
Cost Calculation
The cost will be calculated based on the number of devices that are present in Microsoft Defender for Endpoint. Once per month the number of accounts present in Defender for Endpoint will get fetched.
License Requirements
The following prerequisites need to be met to deliver this service:
- Per-user at least one of the following licenses needs to be present:
- Windows 10 Enterprise E5
- Windows 10 Education A5
- Microsoft 365 E5 / A5 which includes Windows 10 Enterprise E5
- Microsoft 365 E5 / A5 Security
Microsoft Defender for Endpoint More information about Microsoft Licensing can be found here: https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/minimum-requirements?view=o365-worldwide
Microsoft Licenses are not part of Wortell Protect and need to be purchased separately.
Product Requirements
The following requirements are necessary before onboarding this product to our MDR service:
| Requirements | MoSCoW |
|---|---|
| MDE is properly licensed | Must have |
| Operating System updated & patched on regular bases | Should have |
| Applications are updated & patched on regular bases | Should have |
| Devices are centrally managed (for example by MEM / Azure AD) | Should have |
| The Microsoft Security Baseline are in use or used as base | Should have |
Wortell Managed Detection and Response has an extensive onboarding program that will help customers to get compliant with the above requirements. You can read more about our onboarding program over here.