Incident Management
Table of Contents
Introduction
To identify, analyze, and determine an organizational response to cybersecurity incidents, a proper incident management should be in place. Incident management is, according to ITIL, the process of managing service disruptions and restoring services within agreed service level agreements (SLAs)1. In addition, it covers every aspect of an incident across its life cycle.
The incident management lifecycle
Wortell has established a standard procedure for the incident management process. This process is used whenever a cybersecurity incident should occur. The incident management process can be summarized by the following life cycle:
- New – An incident that has been logged but not yet triaged. An incident can be logged through a phone call, email or recording by Vidara. Once an incident is generated in the source system, it will go through initial intake. During this intake, the following action take place:
- Field based prioritization – Based on certain values of fields, a priority can get assigned to an incident: High, Medium, Low.
-
Open – An incident is received in Vidara and assigned to an Engineer. Once the incident is prioritized, a “tier 1 analyst” opens the incident. This analyst conduct triage and setting the Support tier state to “Support tier 1. Triage is classifying an alert in “False Positive”,”Benign Positive”, Undetermined or “True Positive”. Once an analyst opens the incident, the Time To Triage will get applied on incidents. As soon as an analyst close the incident, the Time To Triage will stop. The SLA metrics are explained in chapter 3.
-
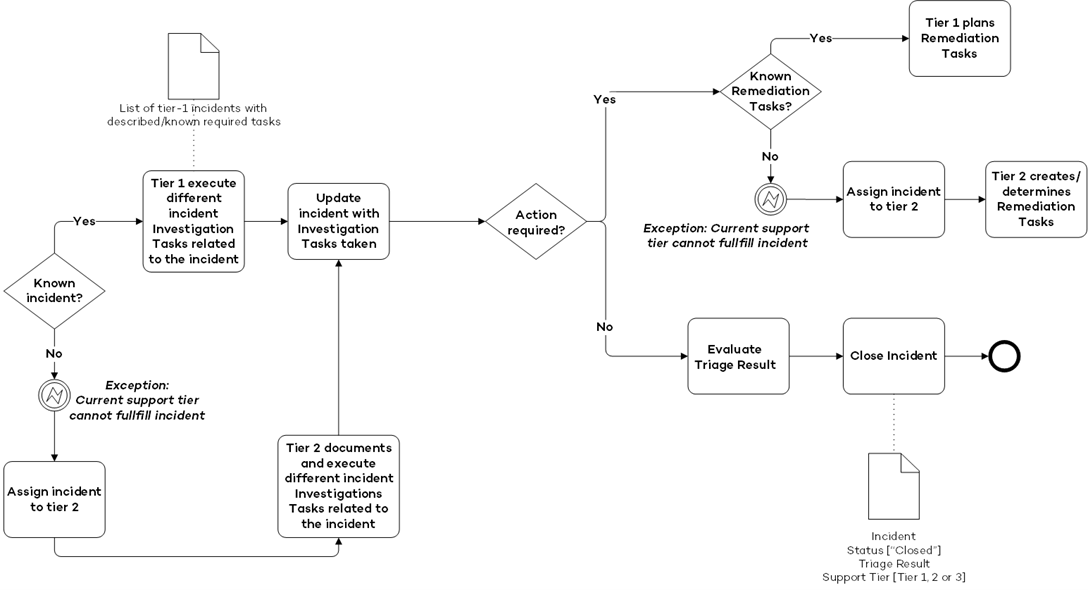
Investigation – An incident that is classified as a “true positive” and need further investigation. In this step additional data is collected. For known incidents, an instruction to fulfill the investigation task(s) is available. If no such instruction is available for this type of incident, escalation to a “tier 2 analyst” will take place. This analyst adds the required tasks and executes them. Based on the collected information, the analyst will determine if remediation actions on the incident is required.
- Remediation – An incident that needs remediation actions. For known incidents, an instruction to fulfill the remediation task(s) is available. If no such instruction is available for this type of incident, escalation to a “tier 2 analyst” will take place. This analyst adds the required tasks and executes them. The tasks include:
- The steps required to isolate the affected resources.
- The steps required to mitigate the incidents.
- The collection of evidence data.
- For critical incidents: further communication while executing the remediation actions (crisis communication).
- Closed - An incident that was closed once the resolution was acknowledged by the customer. Wortell is able to close without customer validation if:
- The incident gets closed after triage.
- The incident gets closed after investigation.
Incident Management Proces
The incident management phases with the corresponding actions are depicted below.
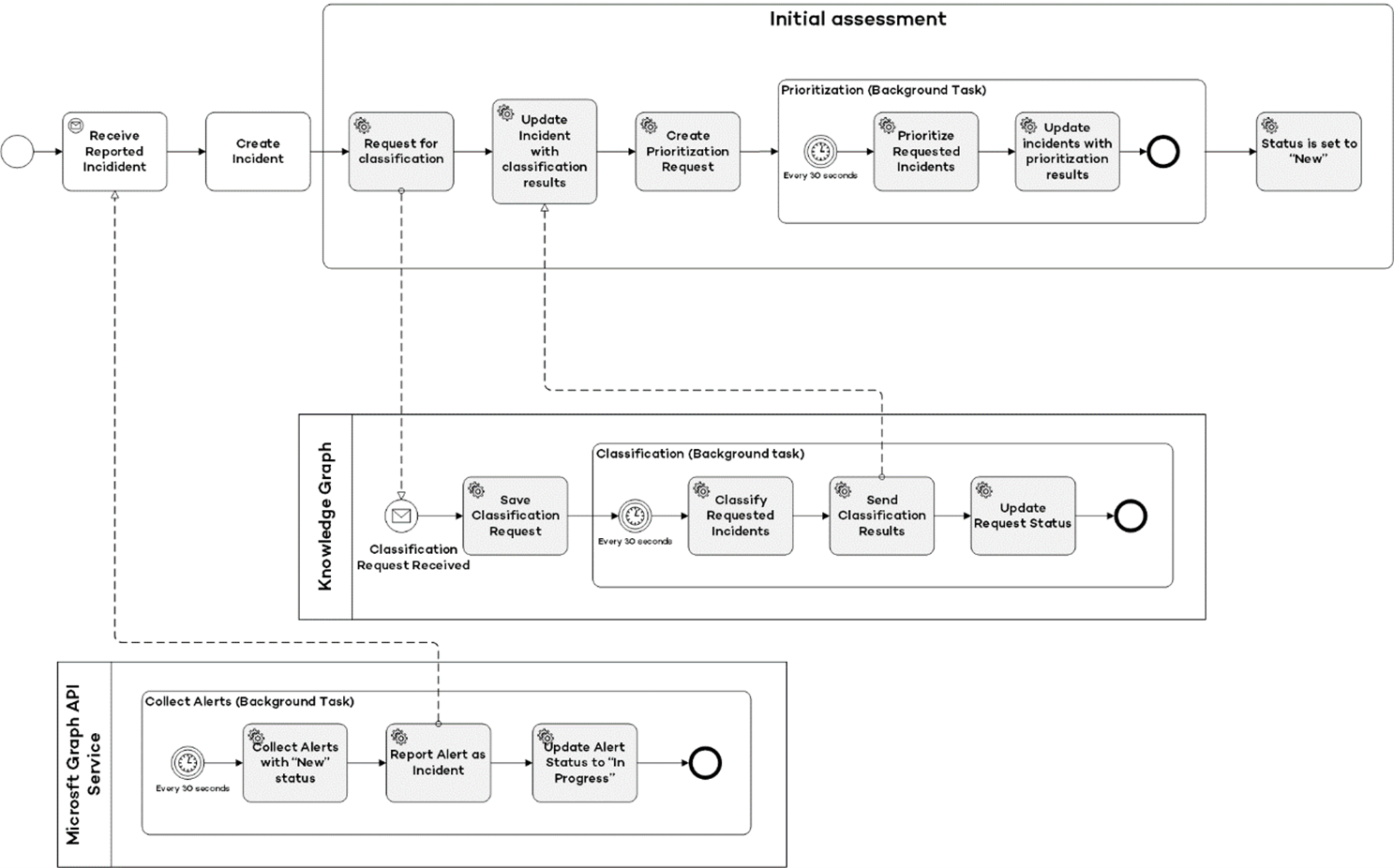
Initial Intake
Each incident that will be handled by Wortell Managed Detection and Response undergoes an intake. This intake proces is used to prioritize an incident and enrich it with the required information for an MDR engineer or automation to be analysed.
Triage
After the initial intake, the incident undergoes triage. As part of the triaging proces, “actionable” incidents are filtered from the “non-actionable” incidents.
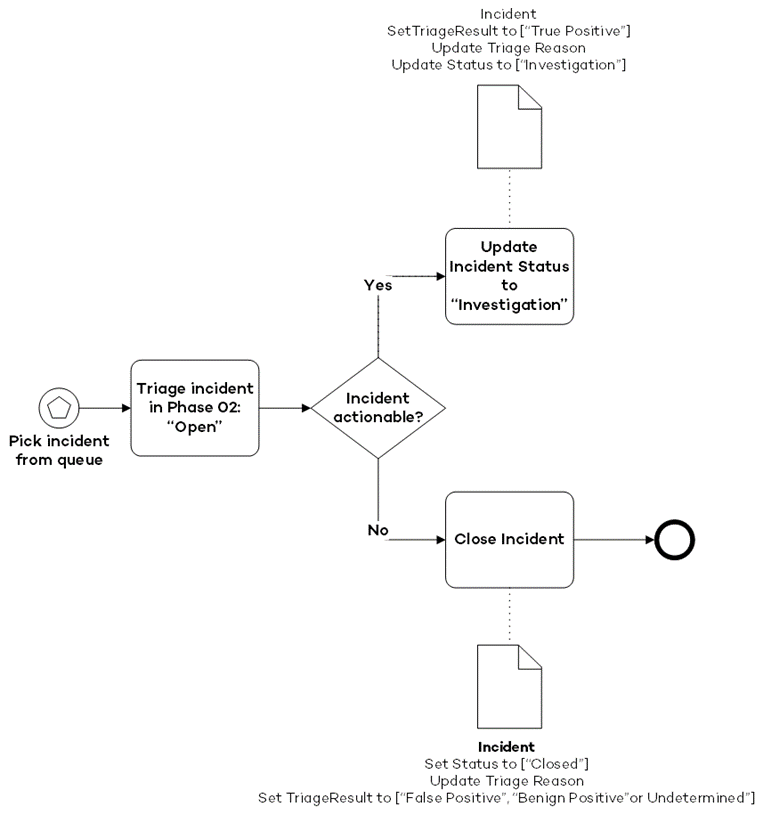
After triaging, each incident will have a triage result. Depending on the triage result, an incident will get investigated or not. The following triage results are available:
| Triage Result | Triage Reason | Needs investigation |
|---|---|---|
| True Positive | Suspicious activity or a malicious action is seen | Yes |
| Benign Positive | Suspicious activity that is expected or explainable | No |
| False Positive (Incorrect alert logic) | Incident created based on wrong alert logic | No |
| False Positive (Inaccurate data) | Incidents that are out of scope of made obsolete by later occurred logs | No |
| Undetermined | Duplicate incidents or informational notifications | No |
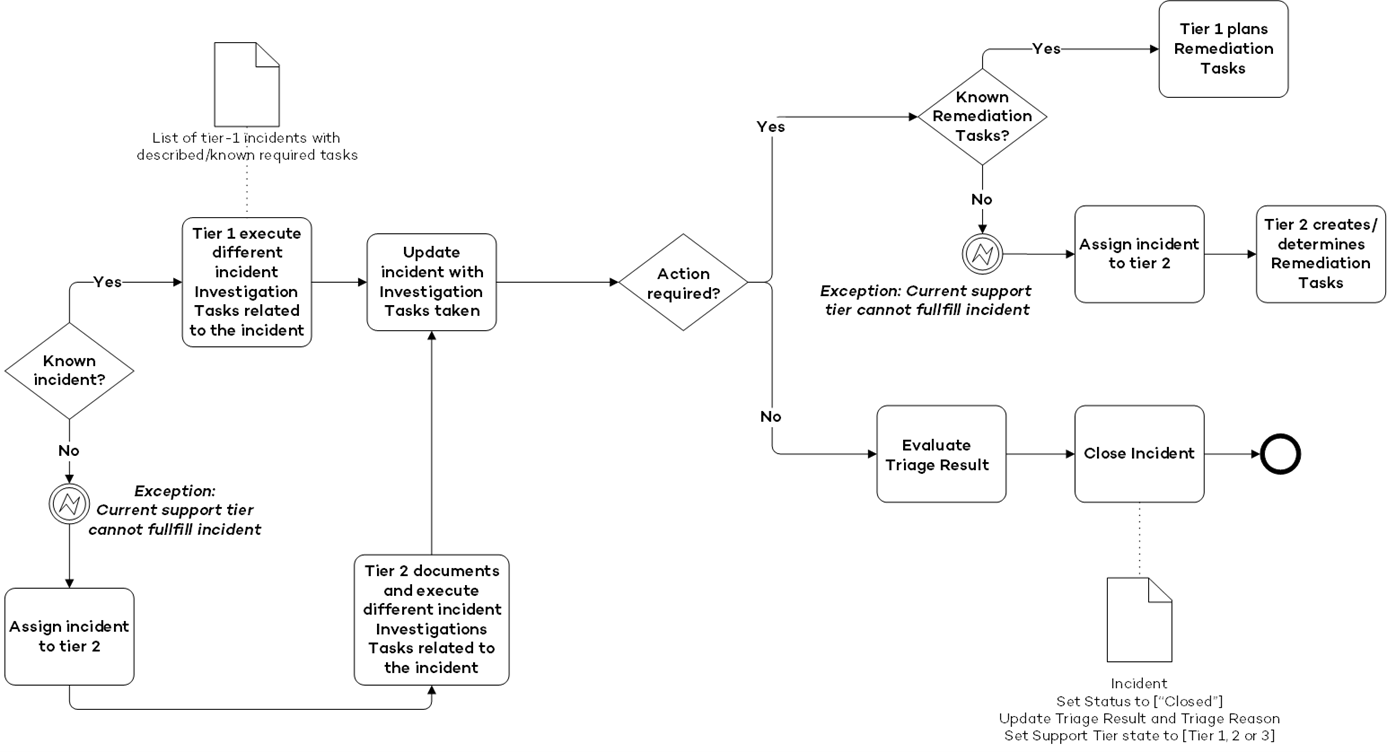
Investigation
When an incident is triaged as “True Positive” it needs to be investigated. The goal of the investigation is to create a plan for the mitigation of this incident.
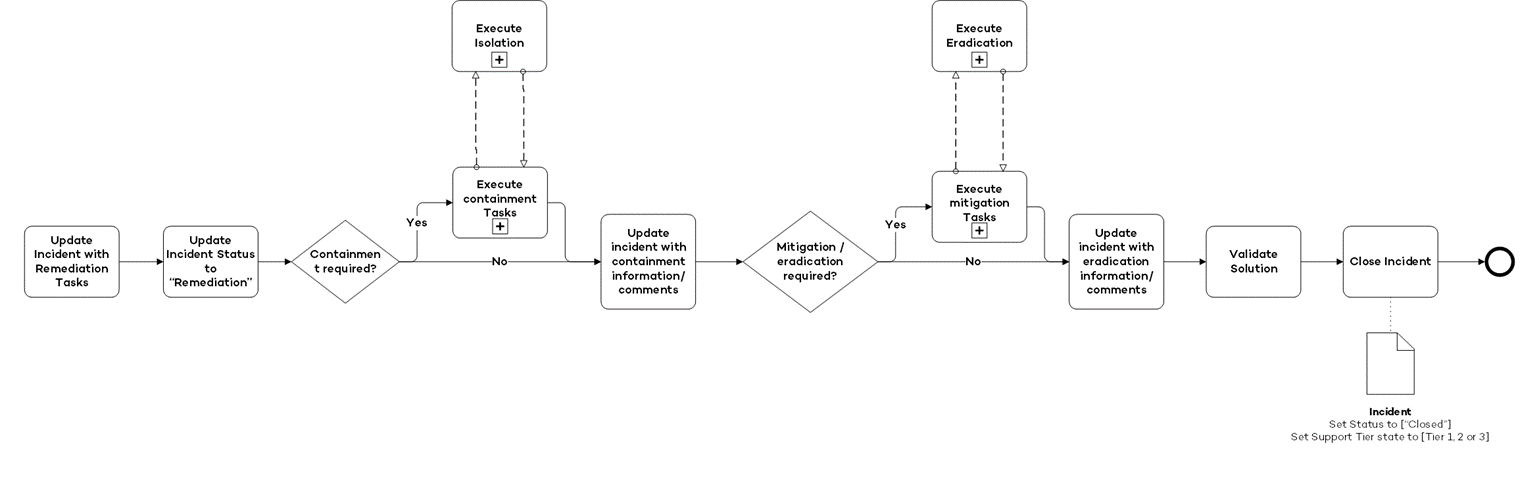
Remediation
After investigation the incident will get remediated. One or multiple remediation activities will get executed to contain and mitigate the incident. Activities to think of:
- Disable user account
- Isolate a machine
- Bloack an IP Address
Support Tiers
Responding to incidents within agreed service level agreements is meant to support incident management that is used by security operations centers (SOC) and in Wortell’s own Cyber Defence Center by their Managed Detect and Response department. Incident Management sits within and across any response process, ensuring all stages are handled.
Wortell MDR uses a tiered model for handling different types of incidents. This model consists out of 4 following tiers of incidents.
- Automation
- Tier 1
- Tier 2
- Tier 3
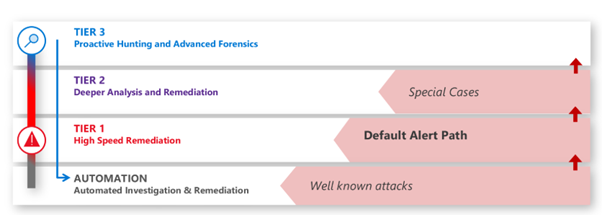
Automation
These are incidents that are completely handled by the Vidara automation platform and require no human interaction.
Tier 1
These are incidents that are not completely handled by the Vidara automation platform and are handled by the Wortell Tier 1 incidents analysts. The following incidents are qualified for tier 1:
- Incidents are documented and following a predefined resolution path.
- The time needed for remediation is less than 30 minutes.
- Incident that do not require changes in the target (customer) environment.
When incidents do net met the criteria to be resolved by tier 1, they will get escallated to tier 2. The following procedure is followed to escallate an incident from TIER 1 to TIER 2:
Tier 2
These are incidents that require more technical knowledge, attention or time in order to remediate them and have the following characteristics
- The incident isn’t covered by a documented Tier 1 procedure
- These incidents require more than 30 minutes to remediate.
- Is a customer request
- An action is required in the customer environment
Tier 3
Tier 3 is a support tier that is being used for:
- The improvement of detection rules
- Execute vulnerability management
- Execute threat hunting sessuibs