Threat Intelligence Management
Table of contents
Introduction
The rapid pace of digital transformation has created many opportunities for businesses to increase profits and grow, but it can also open them up to cyberattacks. Threat intelligence management enables organizations to better understand the global threat landscape, anticipate attackers’ next moves and take prompt action to stop attacks.
Threat intelligence, as defined by Gartner, is “evidence-based knowledge, including context, mechanisms, indicators, implications and action-oriented advice about an existing or emerging menace or hazard to assets. This intelligence can be used to inform decisions regarding the subject’s response to that menace or hazard.”
Goals
This service has the following goals:
- Continuous improve the the quality of detections by using threat intelligence in the alert logic
- Learn from incidents by transforming incident evidence to threat intelligence
- Allow customers to collect their own (sector specific) threat intelligence by using Vidara Honeynet Instances
Requirements
This part of the process description describes the requirements on which the proces should be compliant. For this business service, there are functional and non-functional requirements described.
Functional Requirements
Functional requirements are requirements that describe the functionality of this business service. The following requirements have been defined:
- Wortell Managed Detection and Response should improve detection logic based on earlier incidents. Evidence found at earlier incidents can potentially be transformed to threat intelligence to improve detection logic.
- Wortell Managed Detection and Response should improve detection logic based on (high quality) threat intelligence that is shared in the community.
- A solution should be in place to collect sector and customer spefic threat intelligence to improve detections and be more efficient.
- A solution should be in place to collect generic threat intelligence to improve detections and be more efficient.
Non-functional Requirements
Non-functional requirements are requirements that do not add any functionality but define service attributes such as performance, scalability, security, etc.
- The business service should be designed in such a way that the services can run fully automated; meaning the recurring effort of humans should be kept to a minimum.
- Performance of the service should be measured to address performance related issues or enhance performance.
Proces
The threat management process can be broken down in the following steps:
- Collecting and importing threat intelligence
- Classify threat intelligence with labels like “certainty”
- Post threat intelligence to the customer SIEM
- Use threat intelligence in customer detections
Collecting threat intelligence
Wortell has various ways available to collect threat intelligence. The table below describes the available methods of collecting threat intelligence:
| Methods | Description | Type of TI | Update interval |
|---|---|---|---|
| Vidara Honeynet | Wortell’s own honeypot network for collecting threat intelligence | Generic | Continuous |
| Vidara Honeynet Instance | Wortell’s own honeypot network for collecting threat intelligence in the datacenter/infrastructure of the customer | Sector/Customer specific | Continuous |
| OSINT | Community threat intelligence | Generic | Daily |
| Incident Response | Evidence data of incidents gets transformed to threat intelligence | Sector/Customer Specific | Continous |
Classify threat intelligence
All threat intelligence is stored in Wortell’s threat intelligence systems. Based on the amount of sightings and the collection method, threat intelligence will get classified. This classification describes the certainty that the threat intelligence record is a “true positive.”
Send to SIEM
Depending on collection method, threat intelligence is send to a single customer or send to all customers who are subscribed on Wortell Protect services that include threat intelligence.
- Vidara Honeynet data is send to all customers who have a subscription on Wortell protect services that include threat intelligence.
- Vidara Honeynet Instance data is only send to the customer that hosts the Vidara HoneyNet Instance
- OSINT data is send to all customers who have a subscription on Wortell Protect services that include threat intelligence.
- Incident Response related threat intelligence is only send to the customer to which the incident belongs.
Classification labels (such as certainty) are send to the SIEM so they can be used in detections.
Wortell uses the Graph API to send threat intelligence to the customer environment.
Use threat intelligence in customer detections
Wortell uses Azure Sentinel as SIEM solution. This SIEM solution provides functionality to correlate events with threat intelligence. Customers that have a subscription that includes the Wortell Usecase Library automatically receive use-cases that make use of threat intelligence.
Aside from Wortell’s usecase library, it is possible to create tailor made use-cases that work with your threat intelligence.
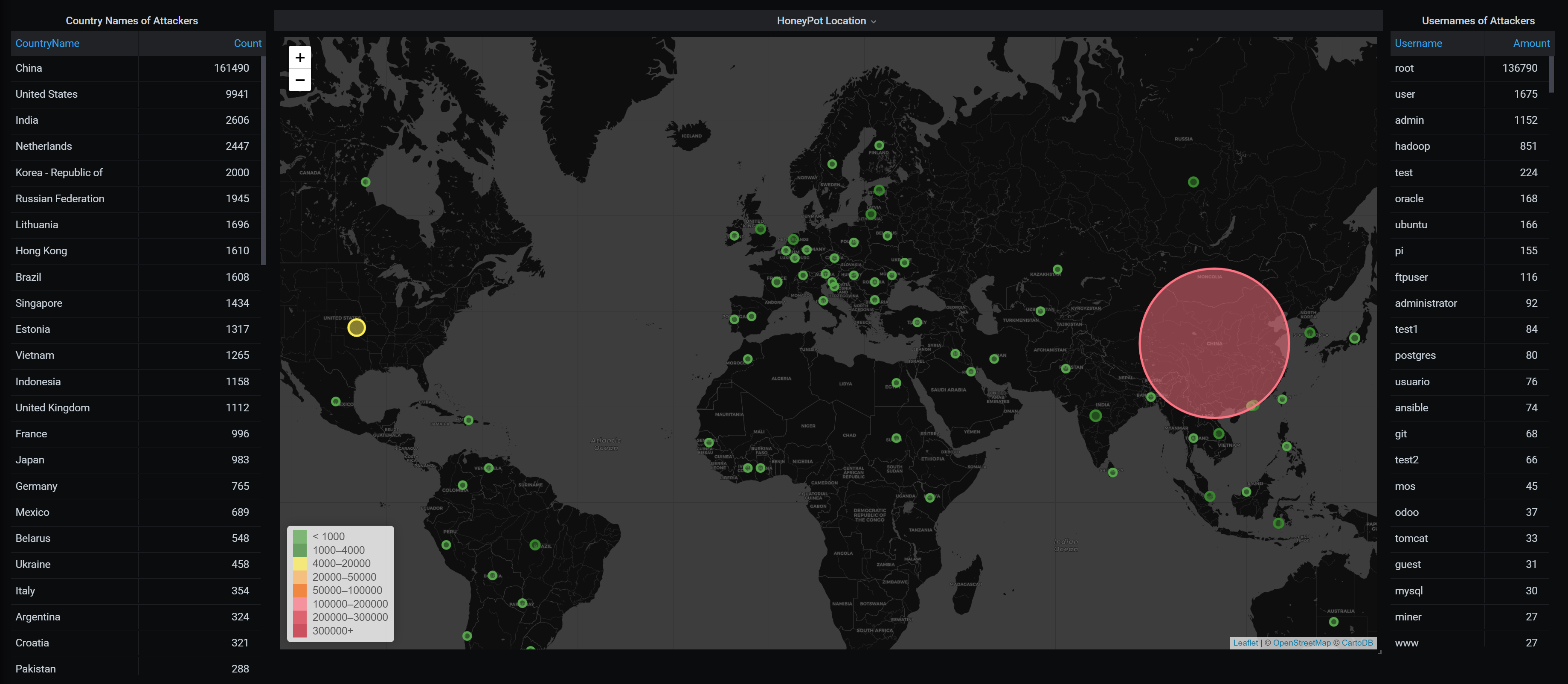
Dashboarding
Wortell Protect customer dashboards are connected with Wortell’s Incident Management System (Vidara) and Azure Sentinel. Wortell uses the Azure Sentinel threat intelligence table to present threat intelligence related dashboards.
Reporting
Wortell Provides a monthly report around threat intelligence. This report is customer specific and includes customer specific threat intelligence.