Azure Server Protect
Table of contents
-
Azure Server Protect
- Table of contents
- Introduction
- SKU’s
-
Features
- Protection against malware on servers
- Protection against ransomware on servers
- File integrity monitoring for Windows and Linux
- Logs collected from Windows and Linux machines were forwarded to Azure Sentinel
- Works with on-premises servers and servers deployed in other clouds
- Vulnerability assessment scanning for servers
- Compliant with NEN & ISO
- 24/7 alert and incident follow-up
- Supported operating systems
- Cost Calculation
- License Requirements
- Product Requirements
Introduction
Azure Virtual Machines (VM) is one of several types of on-demand, scalable computing resources that Azure offers. Typically, customers choose a VM when they need more control over the computing environment than the other choices offer. With this control also comes the responsibility for security.
With Azure Server Protect, Wortell uses Azure Security Center in combination with Azure Sentinel to protect Azure Virtual Machines
SKU’s
| Feature | Azure Server Protect |
|---|---|
| Protection against malware on server | + |
| Protection against ransomware | + |
| Vulnerability assessment scanning for servers | + |
| File integrity monitoring for Windows and Linux | + |
| Logs from Windows and Linux machines forwarded to Azure Sentinel (SIEM) | + |
| Works with on-premises servers and servers deployed in other clouds | + |
| Compliant with NEN & ISO | + |
| 24/7 alert and incident follow-up | + |
Features
Protection against malware on servers
Malware (a portmanteau for malicious software) is any software intentionally designed to cause damage to a computer, server, client, or computer network (by contrast, software that causes unintentional harm due to some deficiency is typically described as a software bug). Devices infected with malware can potentially install ransomware or let attackers have access to business-critical information.
Wortell uses Defender for Endpoint (part of Azure Defender for Servers) as their primary endpoint detection and response solution (EDR). As part of Server Protect, Wortell will investigate and respond (mitigate) all malware that is detected by the EDR solution that is in place. Wortell has trained security engineers who know how to respond to advanced malware. Responding quickly and with a
Protection against ransomware on servers
Ransomware affects an infected computer system in some way and demands payment to bring it back to its normal state. There are two variations of ransomware, being crypto-ransomware and locker ransomware. With the locker ransomware just locking down a computer system without encrypting its contents. Whereas traditional ransomware locks down a system and encrypts its contents. For example, programs such as CryptoLocker encrypt files securely and only decrypt them on payment of a substantial sum of money.
Wortell uses Defender for Endpoint in combination with Azure Security Center and Azure Sentinel to protect your valuable data from malicious apps and threats, such as ransomware. Controlled folder access protects your data by checking apps against a list of known, trusted apps. Controlled folder access works by only allowing trusted apps to access protected folders. Protected folders are specified when controlled folder access is configured. Typically, commonly used folders, such as those used for documents, pictures, downloads, and so on, are included in the list of controlled folders.
Controlled folder access is especially useful in helping to protect your documents and information from ransomware. In a ransomware attack, your files can get encrypted and held hostage. With controlled folder access in place, a notification appears on the computer where an app attempted to make changes to a file in a protected folder. Wortell has trained security engineers who know how to respond to advanced ransomware attacks. Even though a lot of protection is in place to prevent ransomware from running, cybersecurity is still a cat-mouse game. Especially in case of a ransomware incident, it is important to act quickly and correctly.
File integrity monitoring for Windows and Linux
File integrity monitoring (FIM), also known as change monitoring, examines operating system files, Windows registries, application software, Linux system files, and more, for changes that might indicate an attack.
Security Center recommends entities to monitor with FIM. Wortell will implement the following FIM policies:
- File and registry key creation or removal
- Registry modifications (changes in size, access control lists, type, and the content)
Alerts generated by File Integrity Monitoring will get handled by the Wortell MDR team.
Logs collected from Windows and Linux machines were forwarded to Azure Sentinel
Logs from Windows and Linux devices will get forwarded to Azure Sentinel. Wortell will deploy all its related use-cases to Azure Sentinel so a correlation of events and alerts can take place. This also allows the creation of custom (environment-specific) use-cases.
*The creation of tailor-made use-cases is not part of this service and will get invoiced separately.
Works with on-premises servers and servers deployed in other clouds
Aside from servers hosted in Microsoft Azure, other clouds and on-premises environments are also supported. The connection with the on-premises environment or other clouds can be done using Azure Arc or directly by connecting a server to Azure Security Center.
It might be that some features do not work with on-premises environments or other clouds. Due to the on-premises connection, Azure Security Center is only capable of monitoring the activities that are happening inside of a VM. For VMs hosted in Azure, Azure Security Center is also capable of monitoring related resources for a VM (e.g., Network Security Groups, Route tables, etc.)
Vulnerability assessment scanning for servers
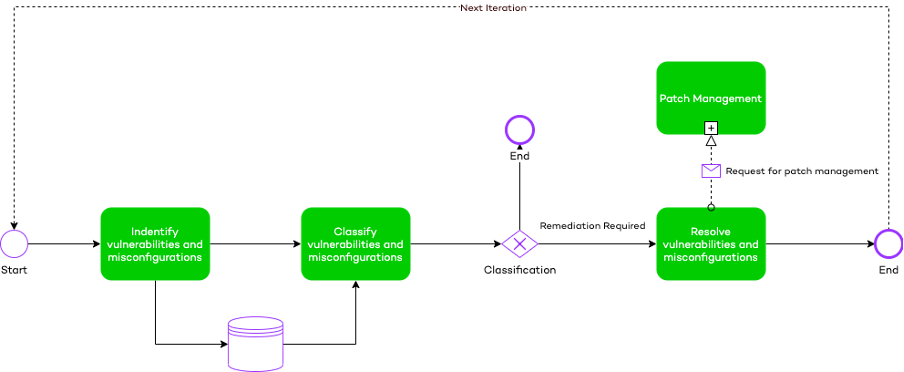
Threat and vulnerability management is the process of identifying, classifying, and resolving misconfigurations and vulnerabilities. In cybersecurity, a vulnerability is a weakness that can be exploited by a malicious actor to gain unauthorized access to or perform unauthorized actions on a computer system. Vulnerabilities can allow attackers to run code, access a system’s memory, install malware, and steal, destroy or modify sensitive data.
To exploit a vulnerability an attacker must be able to connect to the computer system. Vulnerabilities can be exploited by a variety of methods including SQL injection, buffer overflows, cross-site scripting (XSS) and open-source exploit kits that look for known vulnerabilities and security weaknesses in web applications.
A misconfiguration is a setting that is set and will make the IT environment vulnerable. An example of a misconfiguration can be: “a firewall rule that opens port 3389 on a public IP address”. Open misconfigurations become dangerous when legitimate services are exploited through security vulnerabilities or malicious services are introduced to a system via malware or social engineering, attackers can use these services in conjunction with misconfigurations to gain unauthorized access to sensitive data.
Threat and Vulnerability management is proactive, seeking to close the security gaps that exist before they are taken advantage of. If not remediated well, misconfigurations and vulnerabilities will increase the risk and chance of getting attacked.
Wortell provides a process that will reduce the number of vulnerabilities and misconfigurations on your devices. This process will help:
- Reduce the chance of getting attacked successfully by resolving misconfigurations. This will make it harder or even impossible to exploit vulnerabilities.
- Reduce the risk of getting attacked by resolving known vulnerabilities.
- Reduce the impact of an attack by resolving misconfigurations and vulnerabilities. This will make it harder or even impossible to traverse through the IT network.
- Reduce the number of alerts generated by various security products. By resolving vulnerabilities and misconfigurations, sensors are less likely to trigger, because actors are not able to execute actions that will trigger them.
- Report on the risks found in an IT environment.
Compliant with NEN & ISO
ISO/IEC 27001 is widely known, providing requirements for an information security management system (ISMS). Using it enables organizations of any kind to manage the security of assets such as financial information, intellectual property, employee details, or information entrusted by third parties.
24/7 alert and incident follow-up
Cloud Services are important, and attacks are happening during the day and nighttime. Therefore, Wortell has a team of cybersecurity engineers available 24/7.
Wortell has organized the availability of the experts as follows:
- Tier 1: Eyes on-screen during business hours and outside of business hours
- Tier 2: Eyes on-screen during business hours, stand-by outside of business hours
- Tier 3: Eyes on-screen during business hours, stand-by outside of business hours
Supported operating systems
| Windows | Linux |
|---|---|
| Windows Server 2019 | CentOS Linux 8 |
| Windows Server 2019 Core | CentOS Linux 7 |
| Windows Server 2016 | CentOS Linux 6 |
| Windows Server 2016 Core | Debian 10 |
| Windows Server 2012 R2 | Debian 9 |
| Windows Server 2012 | Debian 8 |
| Windows Server 2008 R2 | Debian 7 |
| Windows 10 Enterprise | OpenSuse 13.1+ |
| Windows 8 Enterprise | Oracle Linux 8 |
| Windows 7 SP 1 | Oracle Linux 7 |
| Oracle Linux 6 | |
| Red Hat Enterprise Linux 8 | |
| Red Hat Enterprise Linux 7 | |
| Red Hat Enterprise Linux 6 | |
| SUSE Linux Enterprise Server 15.2 | |
| SUSE Linux Enterprise Server 15.1 | |
| SUSE Linux Enterprise Server 15 SP 1 | |
| SUSE Linux Enterprise Server 15 | |
| SUSE Linux Enterprise Server 12 SP 5 | |
| SUSE Linux Enterprise Server 12 | |
| Ubuntu 20.04 LTS | |
| Ubuntu 18.04 LTS | |
| Ubuntu 16.04 LTS | |
| Ubuntu 14.04 LTS |
Cost Calculation
The cost calculation will be based on the number of servers connected to the Azure Security Center. Once per month the number of servers connected to Azure Security Center will get calculated.
License Requirements
The following prerequisites need to be met to deliver this service:
- Azure Defender for Servers needs to be activated
Microsoft Licenses are not part of Wortell Protect and need to be purchased separately.
Product Requirements
The following requirements are necessary before onboarding this product to our MDR service:
| Requirements | MoSCoW |
|---|---|
| Servers onboarded in Azure defender for Cloud and Defender for Endpoint | Must have |
| No direct internet access on public Ip’s | Should have |